To install a Linux distribution, you have to first download the ISO file, burn it to a bootable media (like USB drive or CD-ROM) and boot it up. The issue lies with the source of the downloaded ISO file. How do you know that the ISO file you downloaded is free of viruses? How do you know that the ISO file has not been tempered by hacker? This is why we need to verify ISO file before we install it on our system.
What is ISO File?
An ISO file (or ISO image) is an archive file that contains data structure similar to an optical disc. It is a file that can be written to an optical disc, like CD or DVD. Nowadays, ISO files are used for distribution of operating system, like Windows and Linux distributions.
How to Verify ISO File?
To be able to verify the ISO file, you will need to obtain a checksum from the file provider. This checksum will be used to verify if the file you have downloaded is correct and has not been tempered. The checksum can be provided as a text file, or just a string of alphanumeric characters.
The most commonly used hash function for generating the checksum is SHA-256. SHA-256 is a cryptographic hash function that will calculate a unique checksum for a file (more like a unique signature) By comparing this generated checksum with the one given by the file provider, you will be able to verify the authenticity of the downloaded file. If there is some discrepancy between the two checksum, then it is possible that the downloaded file has been tempered.
Here’s how you can verify ISO file in Linux:
1. Download the ISO file from the distributor’s website. Also download the SHA256.txt file (if provided. Some distributors will just provide the checksum instead of the text file). Save them to the Downloads folder in your computer. For example, in Linux Mint website, you can download the “sha256sum.txt”.
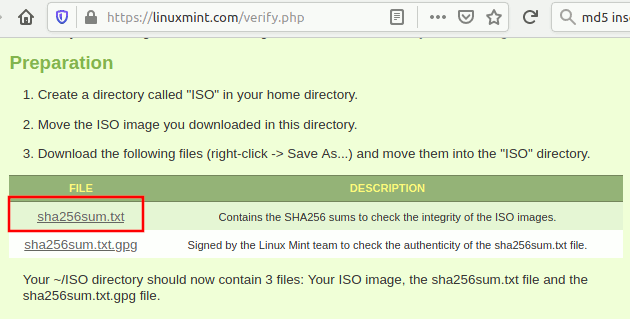
If you open the sha256sum.txt file, you will see strings of alphanumeric characters.
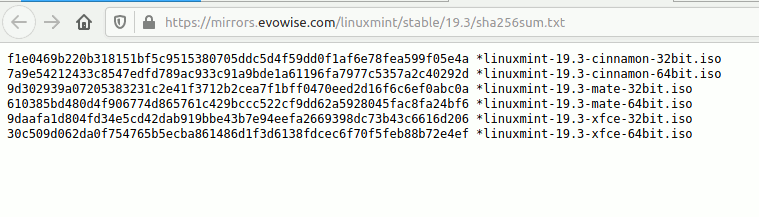
2. Open a terminal in Linux and navigate to the Downloads folder.
<span style="color: #7a0874; font-weight: bold;">cd</span> Downloads3. Type the command to calculate the checksum of your ISO file. In this case, we are using the Linux Mint 19.3 ISO image:
sha256sum linuxmint-19.3-cinnamon-64bit.iso
It should generate a string of characters like this:
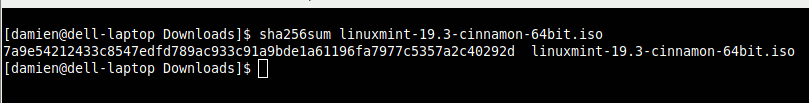
4. Now, compare this number with the string in the sha256sum.txt file. If they are the same, then the ISO file is verified.
Verifying the sha256sum.txt file
While the above steps are easy, there might be a chance that both the sha256sum.txt and ISO files are tempered. To prevent this, we can verify the sha256sum.txt file with a gpg key (provided by the download source).
1. Download the .gpg file from the source (in this case, it is sha256sum.txt.gpg)
2. Open a terminal and go to your Downloads folder:
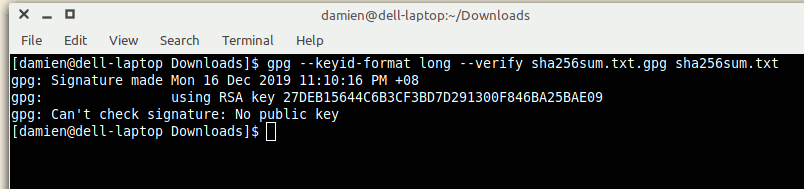
<span style="color: #7a0874; font-weight: bold;">cd</span> Downloads3. Run the command to verify the sha256sum.txt file:
gpg <span style="color: #660033;">--keyid-format</span> long <span style="color: #660033;">--verify</span> sha256sum.txt.gpg sha256sum.txtIf you get the error “gpg: Can’t check signature: No public key”, that means your system doesn’t have the public key to verify this file. You should also see the RSA key listed.
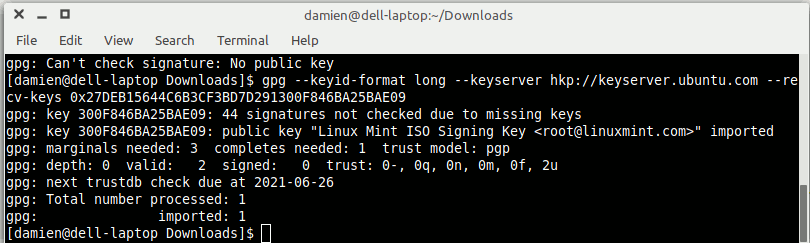
Import the gpg public key with the command:
gpg <span style="color: #660033;">--keyid-format</span> long <span style="color: #660033;">--keyserver</span> hkp:<span style="color: #000000; font-weight: bold;">//</span>keyserver.ubuntu.com <span style="color: #660033;">--recv-keys</span> 0xRSA_KEY_HEREReplace the “RSA_KEY_HERE” with the RSA (or DSA) key listed. Keep the “0x” intact in front of the RSA key.
4. You can now run the above command again to verify the sha256sum.txt file:
gpg <span style="color: #660033;">--keyid-format</span> long <span style="color: #660033;">--verify</span> sha256sum.txt.gpg sha256sum.txt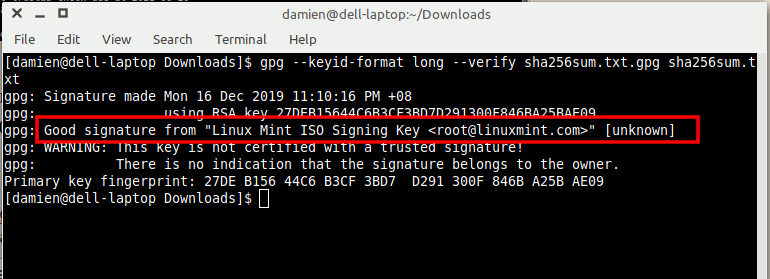
You should see a line like “gpg: Good signature from …” This indicates that the checked file was signed by the owner of the keyfile stated. If the file is not verified, it will report as “BAD”.
You will also see a warning message. You can ignore this as it means that the key is not in your list of trusted source.
Wrapping Up
Verifying an ISO file in Linux is very easy and it is recommended that you do that as often as possible to make sure the file you downloaded has not been tempered.


Be the first to comment! Get the discussion going.